If security is high on your priority list, then you must be concerned about the general operations or activities programs engage in on your computer. On Windows 10, you can take charge of your system to determine which applications are allowed to run. We know of two methods by which you can create the necessary setup.
- If you decide to use “Blacklisting” as a form of control, then your system will let all applications run by default except for those specific programs you added into the blacklist.
- The other method involves the use of a “Whitelist,” and it is generally more secure than the first one we proposed. Here, your computer is set to block every application from running by default, and you get to decide which programs go past the restriction.
Why do I need application whitelisting?
It is common knowledge that the recovery from attacks involving viruses or malware is a lot more difficult than prevention against them. Using a strong protection setup (the one enhanced by whitelisting, for example) is of great importance. After all, malicious items will struggle to wreak havoc on your PC if Windows refuses to let them operate freely.
Whitelisting is a proactive security concept in that it forces Windows to allow the operations of only pre-approved or specified programs once the required setup is in place. We already established what the most practical use of a whitelist entails—blocking or preventing malware and viruses from operating. You might want to know if there are other benefits.
Pro Tip: It is possible to fix many PC issues by using the PC Repair tool. PC Repair is easy to use and reliable Windows optimization software developed to fix hundreds of system issues.
Special offer. About Outbyte, uninstall instructions, EULA, Privacy Policy.
The ability to manage (or control) the resources available on a computer or reduce the activities a system engages in is probably a secondary benefit for some people. What you do on your device is what matters here.
When you set Windows to allow only whitelisted applications to run, then the chances of you experiencing or struggling with system crashes or slowdowns reduces significantly. This change tends to be a result of the reduced demands on your computer since only operations carried out by whitelisted applications are allowed. After all, the whitelisted apps are generally fewer in number than the previous ones allowed to operate without restrictions.
How does application whitelisting work?
The tactic employed in a whitelist setup is incredibly simple considering the powers that come into play. After your created whitelist goes into effect, Windows will compare any program that tries to run against a whitelist, and your system will permit it to carry on only if you have included it on the specified list.
You might have started thinking about a malicious program disguising itself (to pretend that it is an item on the whitelist). Well, we have to tell you that a secondary measure (hashing) is available for use to verify the integrity of programs that attempt to run.
Considering the improvements in malware, their volume, and the level of attacks they are capable of executing these days, we can easily claim that is impractical (or borderline impossible) to maintain a comprehensive or exhaustive list (blacklist, for emphasis) of virus definitions or malicious programs. Therefore, your preferred approach anytime should be whitelisting, which works in reverse to blacklisting.
Nevertheless, it is imperative you understand that whitelisting is not a complete or all-encompassing solution to the problem of security on Windows. It cannot replace primary security measures or guidelines. Not yet, at least. We hope you employ whitelisting to work with standard protection technologies. This way, it acts as a supplement that enhances your computer’s security.
How to use software restriction policies on Windows 10?
In this guide, we will guide you through several whitelisting procedures and operations you can carry out to improve the security of your computer. We will show you how to set up path rules on Windows 10, how to add new regulations whenever you install a new app, and so on.
You will whitelist applications through Software Restriction Policies available on Windows 10. The instructions provided here are geared towards individual users, but a good number of the procedures have equivalents that Enterprise users can take advantage of to carry out the similar operations on a Windows domain.
You might find the setup to be a bit cumbersome initially, but as time goes on, you will get used to it. Your time and effort will definitely pay off because after you set up a whitelist, the chances of your computer getting damaged by the activities of viruses or malware become significantly lower than before.
You will configure the whitelisting options you need through Security Policy Editor which controls the settings for Local Security Policy.
Follow these instructions:
- Hit the Windows button on your keyboard or click on the Windows start icon that is always present on your desktop screen. In the text field present, you must input the following code to do a quick search for it: secpol.msc
- From the list of results that appears, click on Secpol.msc
- The Local Security Policy program window should be up and running by now. Now you can begin your work to create the whitelist. From the list of items on the left pane (Security Policies), click on Software Restriction Policies.
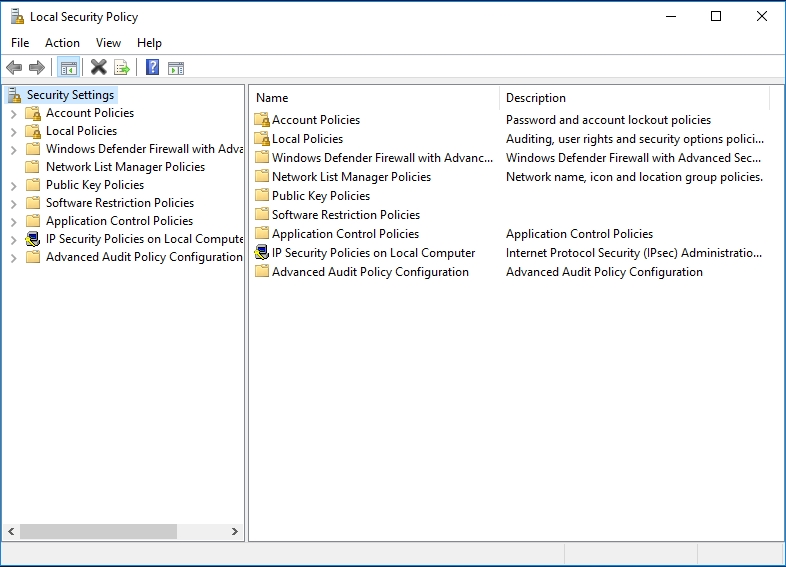

- If you have never created a software restriction policy before, you will see a message stating that there is no defined software policy on the right pane. Continue with the steps below to create a new policy.
- Right-click on the Software Restriction Policies category or icon (on the left pane). From the short list of options that appear, select New software restriction policies. The options for a new software restriction policy will appear on the right pane
Now you must begin your work by configuring the Enforcement setup. In this section, you will get to specify general settings on how the restriction policies should be configured. Continue with the instructions below:
- Go through the items you see on the right pane. Click on Enforcement. The Enforcement Properties window should come up now. There is no need to change anything here. This way, you get to avoid the issues that might result from the blocking of DLL files. Regardless of what we said, you are free to make alterations or changes if you deem them necessary
- After you finish configuring the necessary settings, click on the OK button. Windows should take you back to the main Software Restrictions Policies window you saw earlier.
It is time you defined what file types will be considerable executables that Windows is supposed to block or stop from running:
- Click on the Designated File Types object. The Designated File Types Properties window should appear now. You will find a long list of file extensions or formats. Carefully go through the list and take note of things
We believe that the list you are seeing is not as comprehensive as it should be. Some modifications to it are in order—you must delete some file formats to avoid complications, and you must add some extensions to improve the definition for dangerous items that Windows must block. The instructions below will guide you through:
- First, we recommend that you remove the LNK extension. Scroll down and locate it. Click on it to highlight it, then click on the Remove button to get rid of it. If you refuse to delete this particular extension, then all the shortcuts you have on your computer will become unusable after your whitelist setup becomes active.
- Now, we advise that you include some extra extensions that attackers employ for the installation of viruses or malware. To add an extension, all you have to do is input the extension into the text field for File extension and click on the Add button beside it. You do not have to type in Period (.) as only letters are needed.
For example, if you want to add the extension required to exclude PowerShell scripts, you must input “PS1” into the field without the quotes, then click on the Add button. Here is the full list of the designated file types we want you to add so that Windows can block their corresponding program forms from running:
- PS1
- SCT
- JSE
- VBE
- VBS
- WSF
After you finish adding the listed extensions, click on the Apply button, then click on the OK button to save the changes you have just made. You should be back at the main menu for the Software Restriction Policy
- Now, you must move on to create the default policy that determines if the selected file types will be blocked or allowed to run automatically. Here you go:
- Click on Security Levels (one of the items from the list on the right pane). You will see 3 options on your current screen. They are fundamentally different levels of security that you can apply to your software restriction policies. A basic understanding of the available options comes in handy here.
- Disallowed: If you go with this option, then Windows will not allow any program to run regardless of the rights of the user requesting access except for the applications you selected to run based on the rules you configured
- Basic user: When this option is selected, all programs will be executed with the privileges afforded to regular users rather than the ones associated with administrative rights
- Unrestricted: With this option active, Windows will allow all programs to run as they should without any restrictions
- You are here to block all programs from running (excluding the ones you have allowed to operate). Therefore, the Disallowed option is the one of interest to you currently. Double-click on the Disallowed object
- The Disallowed Properties window should be up now. Click on the Set as default button you see. Windows will now block all applications by default. Click on the Apply button to continue. Click on the OK button. Windows should now move on to save the changes.
- Windows should take you back to the Security level list screen. You can perform a simple operation to verify that the setup you created has become active. Minimize your current program window. Try to open any application. You should see a message stating that the program is blocked by group policy and that you should contact your system administrator.
If things did not go the way we described, then you most likely missed something along the way. Go through the instructions above once more, but this time you should be more careful while you carry out every single operation.
At this stage, we expect that you have successfully configured the setup that instructs Windows to block all applications from running. It is time you moved on to set the rules that will enable the legitimate applications you have to operate without problems.
How to use an application whitelist policy on Windows 10?
Here, you are going to learn how to create rules that define the whitelist policy. If you went through the explanation we gave, you might have figured out that the Software Restriction Policies are active already. They are blocking all executables apart from the ones located in these directories: C:\Program Files and C:\Windows
In theory, Windows whitelists the stated paths automatically (without any input from you), and this happens for a good reason. If you want to stop viruses and malware from taking advantage of this whitelisted file path to engage in their nefarious activities on your device, you need to start logging into Windows, using a standard user account. Administrator accounts constitute a weakness in this regard.
Well, it is time you whitelisted other applications since you need a good number of programs to do your work on Windows. You will have to make additional rules for every folder or application you intend to use.
To serve as an example, we are going to show you how to create the required rule for this path: C:\Program Files (x86). The folder here contains the vast majority of applications that users need to whitelist for the 64-bit version of Windows in most cases. We would like to assume you are one of them. Here are the instructions you need to go through:
- Go back to the Local Security program window (if you minimized it earlier). From the list of items present on the left pane, click on Software Restriction Policies. Click Additional rules
- You will find the two default rules we mentioned earlier (Windows created them automatically without any input from you). You are going to add yours now. Right-click on any area void of objects or icons. From the list of options that show up, click on New Path rule
- The New Path Rule window should be up now. Since you want to create a path rule for the items located in this directory C:\Program Files (x86), all you have to do is copy and paste C:\Program Files (x86) into the field for Path.
- Select Unrestricted as the security level (we believe this is the default option, anyway, which means that the programs contained in the selected path are allowed to run without issues). You can enter a short description for the rule you chose if you want to (especially if you know what you are doing)
- Click on the Apply button as usual. Click on the OK button. Windows should store the changes now. The rule should become active immediately. You should be back at the Local Security Program window where you will see the new rule you just added under the Additional rules section. This event can serve as a confirmation that you carried out the required operations correctly.
If you need to make new rules for games or other programs located in a directory that does not fall under the C:\Program Files (x86)
path, you must follow the same steps above, input the new path into the required field, then save the changes. For example, users who play titles through Steam will definitely be interested in adding an unrestricted rule for items contained in this path: C:\Program Files\Steam.
Things to take note of when you are creating new rules to whitelist programs on Windows 10
- If you create a rule for a specific path, you must know that Windows will allow all the items contained in the destination folder and even those in the subfolders (and so on) to run freely. If the parent folder becomes unrestricted, the subfolders acquire the same powers or attributes.
For example, we mean that if you create a path rule for C:\MyStuff directory to allow all the items there run without restrictions, then programs or applications contained in somewhere like C:\MyStuff/Bestgames will run without issues. The same thing applies to objects contained in paths like this one: C:\MyStuff\BestGames\SecretTitles\AdventureGames\Arcade.
- You can use wildcards to streamline the rules. This way, you get to define the exceptions more clearly. If you want to denote a single wildcard character, you will employ the Question mark (?). If you plan to work with a series of wildcard characters, then the asterisk (*) is what you need instead.
We recommend that you use a wild path rule like this C:\MyStuff\*.exe if you have a folder of executable files that you wish to whitelist. With this rule in place, Windows will allow all files with the .exe extension to run without restrictions, but it will block the executable files contained in the subfolders of that path from running.
If you wish to allow a specific item to run instead, then you must create a path rule for the single wildcard character like C:\MyStuff\PlayGame1.exe. After you set this rule, Windows will allow PlayGame1.exe contained in the C:\MyStuff directory to run, but it will block other files (PlayGame2.exe) saved in the same location from running.
- You can also set broad or far-reaching exceptions. If you want to allow the executables contained in a specific folder run without restrictions regardless of what user profile is logged in on Windows, then you can specify a rule like this: %UserProfile%\SpecialFolder\*.exe
With the stated rule in place, Windows will allow all the executables in the indicated folder to run. Invariably, an expansion for %UserProfile% to the correct location takes place for every user account logged into your computer.
- Finally, if you an advanced user who wants to run executable files shared through a network, you will need to create a rule to specify the full UNC path. Here is an example of what we are talking about: \\Dev-server\Files
Other types of Software Restriction Policy rules
Although you worked on and applied a good number of rules to whitelist applications, you might be interested in knowing other forms of exceptions. Well, your interest (if it exists at all) largely depends on what kind of user of you are. Here are some of the rules we are referring to:
Certificate Rule:
We expect you to have figured out what kind of rule this is. In case you are yet to, then it is our job to tell this rule is used to create exceptions that Windows applies to allow the running of only executable files signed by a specific security certificate.
There are significant downsides associated with the implementation of this particular rule, though. According to Microsoft, users might suffer performance issues if they use Certificate Rules.
Hash Rule:
If you want Windows to allow a file to run regardless of where it is located, then this rule is what you have been waiting to see. To make use of this rule, all you have to do is select the executable file in view to allow the retrieval of the information by SRP that Windows will save as part of the rule.
After the rule becomes active, if an executable file on your system (that matches the stored file hash and information) tries to run, Windows will let it operate freely.
Tip:
You probably ended up on this page because you wanted to learn how to apply whitelist policies on Windows 10. With the knowledge you acquired here, you can do great things. We implore you to go a step further to download and run Auslogics Anti-Malware.

This superb program is well capable of running without having to interfere with the operations carried out by your antivirus (if you have one in use already). With the recommended app in place, your system gets an extra layer of protection to keep out threats, and through the new setup, your PC becomes more protected than ever.